Paper accepted at ACM TOMM: Counterfeiting Attacks on a RDH-EI scheme based on block-permutation and Co-XOR
Authors: Fan Chen (Southwest Jiaotong University, China), Lingfeng Qu (Guangzhou University, China), Hadi Amirpour (Alpen-Adria-Universität Klagenfurt), Christian Timmerer (Alpen-Adria-Universität Klagenfurt), and Hongjie He (Southwest Jiaotong University, China)
Journal: ACM Transactions on Multimedia Computing Communications and Applications (ACM TOMM)
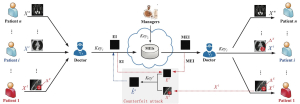
Abstract: Reversible data hiding in encrypted images (RDH-EI) has gained widespread attention due to its potential applications in secure cloud storage. However, the security challenges of RDH-EI in cloud storage scenarios remain largely unexplored.} In this paper, we present a counterfeiting attack on RDH-EI schemes that utilize block-permutation and Co-XOR (BPCX) encryption. We demonstrate that ciphertext images generated by BPCX-based RDH-EI are easily tampered with to produce a counterfeit decrypted image with different contents imperceptible to the human eye. This vulnerability is mainly because the block permutation key information of BPCX is susceptible to known-plaintext attacks (KPAs). Taking ciphertext images in telemedicine scenarios as an example, we describe two potential counterfeiting attacks, namely fixed-area and optimal-area attacks. We show that the quality of forged decrypted images depends on the accuracy of the estimated block-permutation key under KPA conditions. To improve the invisibility of counterfeit decrypted images, we analyze the limitations of existing KPA methods against BPCX encryption for 2×2 block sizes and propose a novel diagonal inversion rule specifically designed for image blocks. This rule further enhances the accuracy of the estimated block-permutation key. The experiments show that, compared to existing KPA methods, the accuracy of the estimated block-permutation key in the UCID dataset increases by an average of 11.5%. In the counterfeiting attack experiments on Camera’s encrypted image, we successfully tampered with over 80% of the pixels in the target area under the fixed-region attack. Additionally, we achieved a tampering success rate exceeding 90% in the optimal-region attack.